The fake Microsoft Security Alert is a common tech support scam affecting Windows users. Malicious websites use fake pop-up warnings posing as Microsoft to trick users into calling fraudulent phone numbers. By instilling fear of malware and hacking, scammers aim to gain remote access and steal personal data and money.
This comprehensive guide will dive deep into how the Microsoft Security Alert scam works, real examples of the phishing pop-ups, and most crucially, how to identify and avoid becoming victimized. We’ll also provide best practices if you encountered any suspicious activity or may have downloaded malware.
This Article Contains:
Overview of the Fake Microsoft Security Alert Scam
The Microsoft Security Alert scam is a widespread threat for all Windows users. Through fake pop-up alerts, scammers impersonate Microsoft in order to deceive users into allowing remote access to their computers.
Here’s an overview of how the scam typically operates:
- Malicious redirects lead to fake Microsoft security pop-ups
- Pop-ups use logos and urgent warnings about viruses
- Scare tactics pressure users into calling tech support numbers
- Numbers route to overseas scam call centers, not Microsoft
- Callers are tricked into providing remote computer access
- Scammers install spyware, steal data, encrypt files for ransom
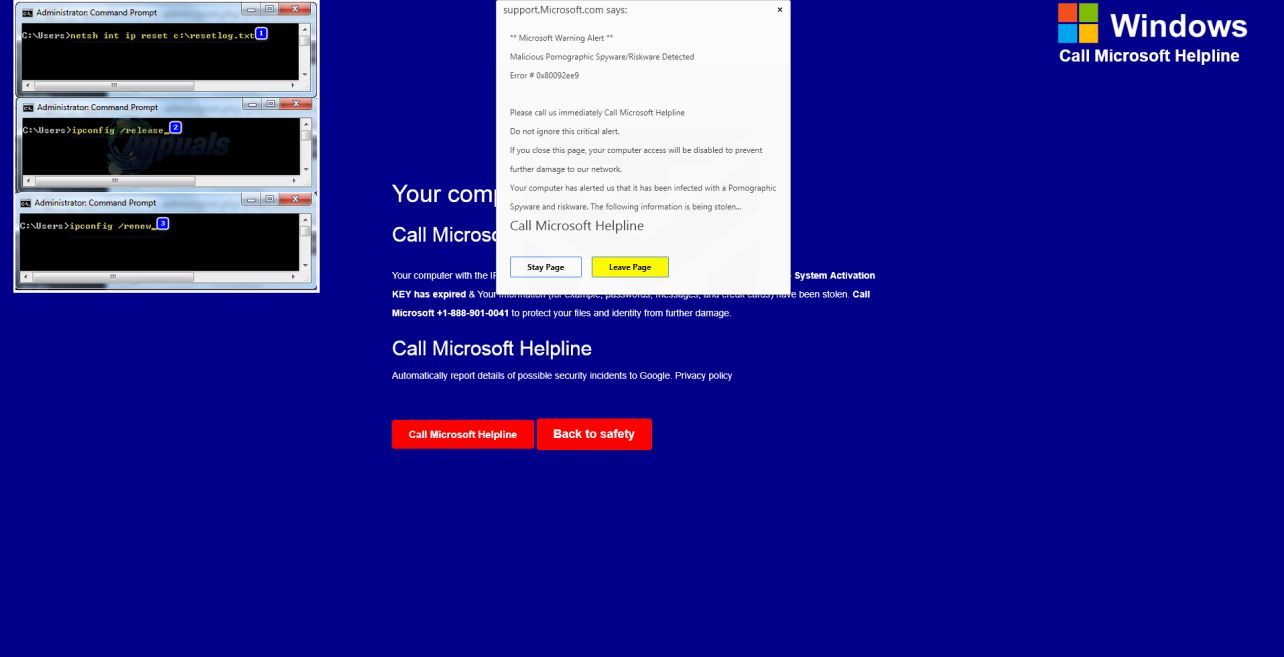
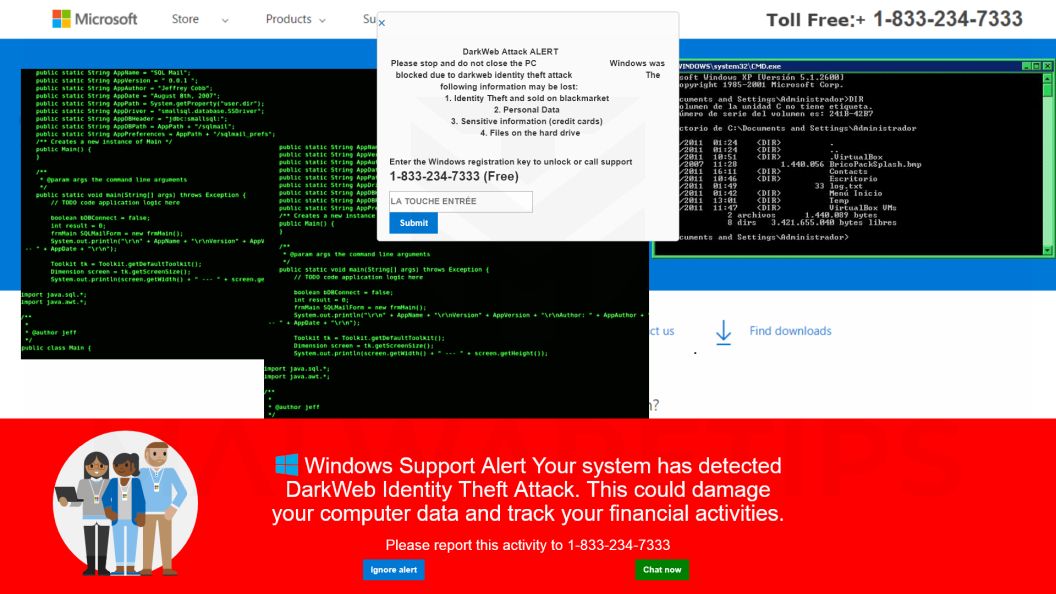
This scam is also known as the “Microsoft technician virus” and “Windows Defender security alert” phishing scam. The pop-ups are very convincing at first glance, leveraging the Microsoft brand and alarms about malware to make the warnings seem credible. But it’s all an act aimed at scaring regular users into calling the fraudsters.
Once remote access is gained, scammers have full control to install malware, take personal information, lockdown computers with ransomware, or trick victims into unnecessary payments. Microsoft would never contact users this way or use such deceptive pop-up warnings.
Common Traits of Fake Microsoft Security Alerts
While the specific messages vary, most fake Microsoft alerts share certain characteristics:
- Microsoft or Windows logos and branding
- Urgent warnings about viruses, malware or hacking
- Threats of stolen data, identity theft or ransomware
- Toll-free numbers with area codes like 844 or 888
- Poor grammar, spelling and wording errors
- Requests for immediate action to call tech support
Examples of Fake Microsoft Security Alerts
To illustrate what these fraudulent pop-ups look like, here are some examples:
- “ALERT FROM MICROSOFT: Your PC is infected with 8 viruses! Call toll-free 844-245-1245 immediately to prevent file deletion and identity theft.”
- “Microsoft Firewall Alert: Hackers have accessed your computer! Call 888-867-1432 now to speak with a Windows security expert before all data is compromised.”
- “URGENT WARNING FROM MICROSOFT – Your Windows license has expired allowing virus entry. Call 833-712-8658 before your PC is fully corrupted!”
- “MICROSOFT COMPROMISED – Windows Defender has detected RANSOMWARE on your PC! Call tech support immediately 844-426-0392 before all files are encrypted!”
As you can see, the pop-ups leverage the Microsoft brand and urgent threats about malware, hacking and ransomware to frighten users. But again, it’s all just a facade to trick you into giving up remote access. Microsoft would never send alerts like these.
Now let’s examine the scam details even further.
How the Microsoft Security Alert Scam Works
Cybercriminals are using an array of deceptive techniques to target Windows users with fake security alerts. Here’s an in-depth look at exactly how the scam unfolds:
Step 1: Victim Lands on Malicious Website
The sequence often starts with a user visiting a compromised website harboring malware. Some examples of dangerous sites include:
-Torrent sites offering illegal downloads of movies, music or software
-Offshore and unlicensed gambling platforms
-Adult websites with inappropriate content
-Bogus technical support sites
-Suspicious pages for “free” movie and TV streaming
These types of websites are infested with malware and redirects. The user may click a link or button that seems harmless, only to suddenly get rerouted.
Step 2: Fake Microsoft Pop-up Appears
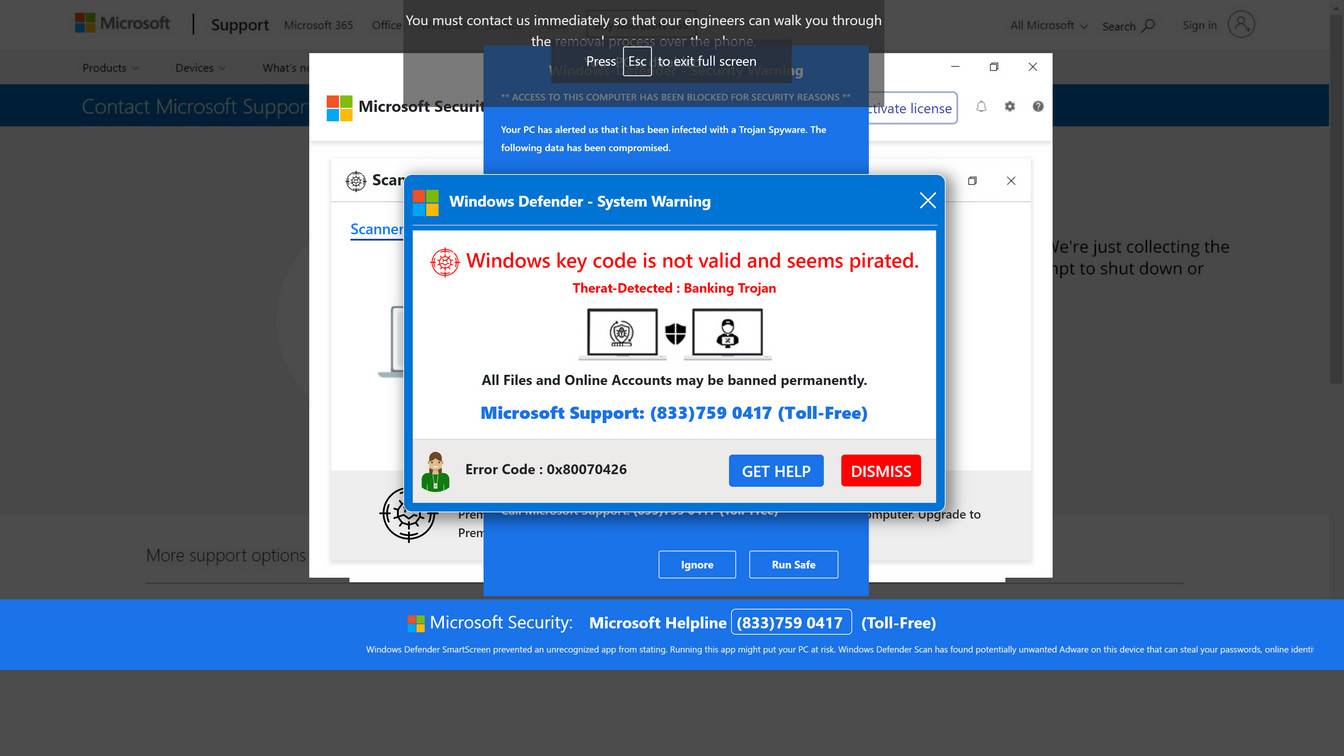
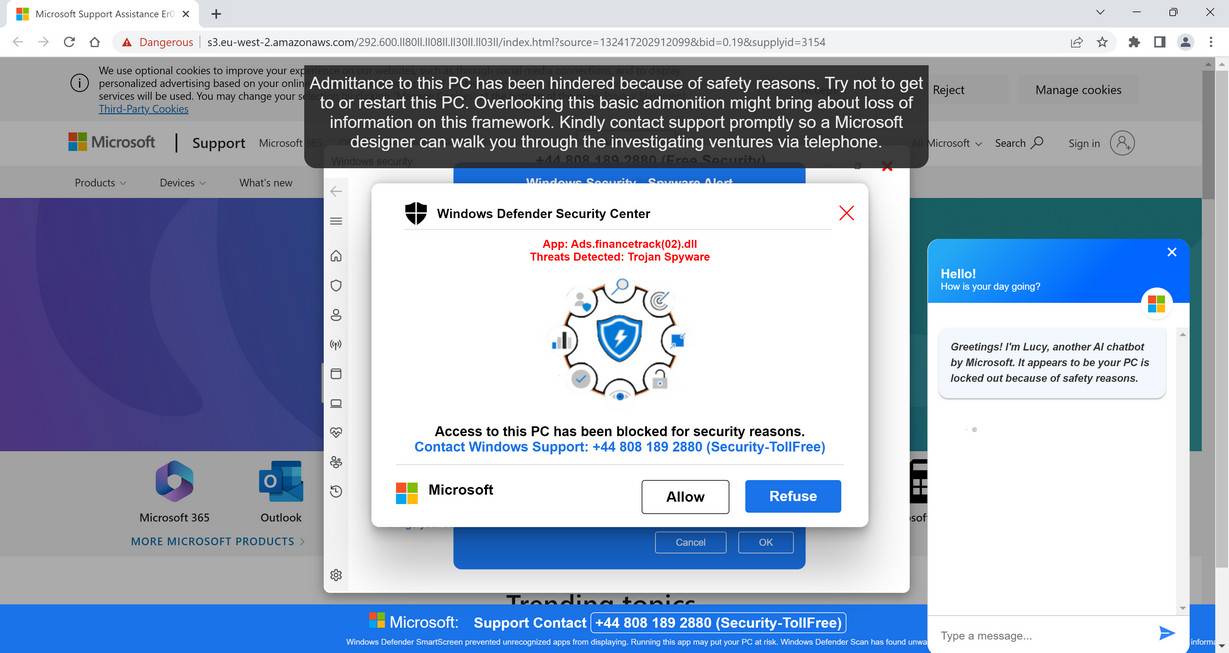
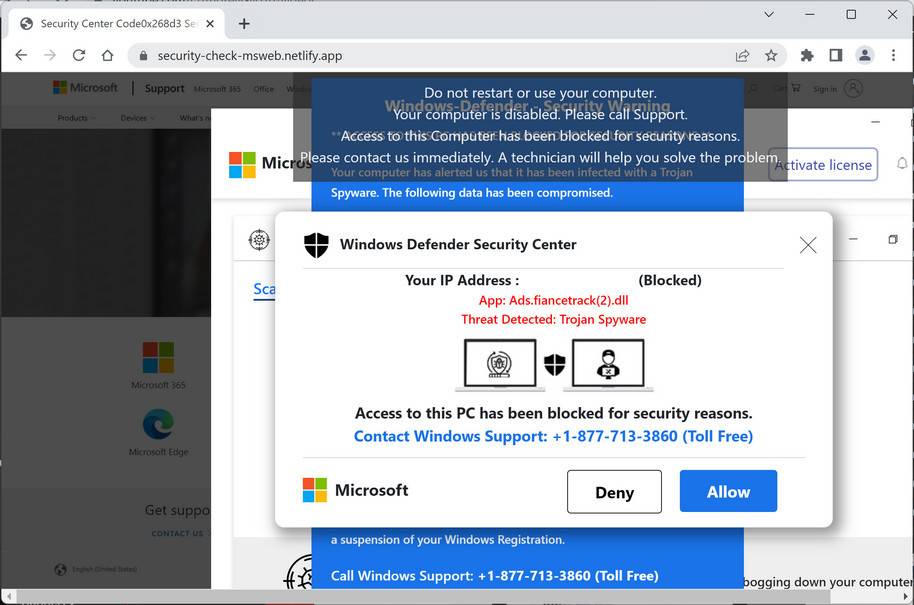
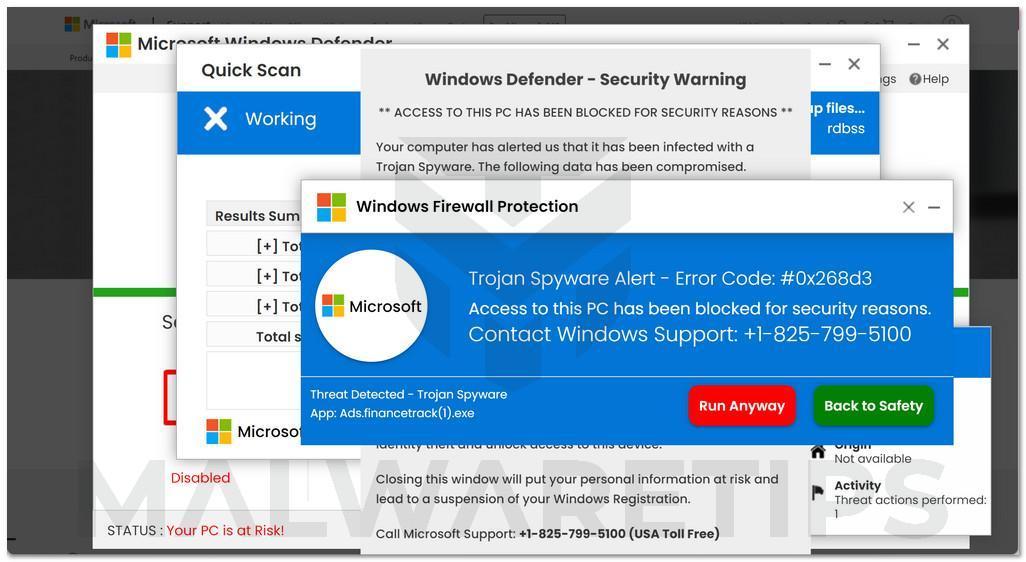
Once redirected, the fraudulent pop-up alert appears on-screen pretending to be from Microsoft. The alerts look like real warnings with Microsoft logos, colors and mentions of security threats.
Visually, pop-ups are engineered to mimic the classic Windows blue screen of death. The goal is to impatiently alarm the user into calling tech support right away.
Step 3: User Calls the Tech Support Number
Spooked by warnings of computer infections, hacking and stolen data, the user calls the tech support number shown on the pop-up.
But in reality, these numbers route internationally to scam call centers in India rather than any legitimate Microsoft operation.
Step 4: Scammer “Confirms” the Security Threat
When the user describes the pop-up alert, the overseas scammer will confirm the computer is under active attack by hackers, infected with viruses, or already compromised by malware.
The scammer insists the threats are real and an immediate remote software connection is required to assess the damage and get the computer cleaned.
Step 5: Remote Access Software is Installed
Following the scammer’s instructions, the user is directed to a website to download remote access software like AnyDesk.
The scammer will provide a connection code to enter into the software, allowing them to take control of the victim’s computer remotely.
Step 6: Scammer Steals Data and Money
Once connected, the scammer has full access to files, passwords, accounts and payment information. Common attacks include:
- Installing actual malware and viruses
- Encrypting files and holding computer ransom
- Stealing login credentials and personal information
- Transferring money out of accessed financial accounts
- Logging into and changing passwords for accounts
- Tricking the user into unnecessary payments for fake “security software” or tech support services
In summary, the pop-ups are simply a lure to get users to hand over their computer. The real motives are identity theft, installation of malware, and extortion.
What to Do If You Get a Fake Microsoft Security Alert
If you see one of these fraudulent pop-ups on your Windows PC, here are the immediate steps to take:
Close Out the Alert Right Away
Do not call the number or click anything in the alert window. The warnings are fake and only lead to scams.
Disconnect from the Internet
Exit any open browsers and cut off internet access on affected devices to terminate connections.
Scan for Malware Infections
Run a full system antivirus scan to uncover and remove any malware, viruses or remote access tools that may have already been installed.
Change All Passwords
Reset the passwords on any accounts that were logged into that device, especially financial accounts, email, and ecommerce sites. Enable two-factor authentication where possible.
Contact Banks and Credit Cards
If there’s chance your financial information was exposed, inform your bank and credit card companies to watch for fraudulent charges.
Avoid Suspicious Websites
Refrain from visiting shady sites where tech support scam pop-ups are most prevalent, like illegal streaming and torrent platforms.
The crucial steps are closing down internet access, scanning for malware, and changing passwords as a precaution in case viruses or spyware were already installed before the pop-up appeared.
What to Do If You Already Called the Scammers
If you already contacted the scammers and provided remote access before realizing it was a scam, remain calm and take these steps right away:
Terminate the Remote Session
If the scammer is still connected, immediately end the remote access session through your software’s management console or disconnect your PC’s internet.
Run Antivirus Scans
Perform full scans with your antivirus software and the Windows Defender tool to remove anything suspicious the scammer may have planted, including remote access trojans. Delete all infections detected.
Change All Account Passwords
For any accounts you accessed while the scammer had remote access, change the passwords immediately. Enable two-factor authentication if available.
Contact Your Bank
Alert your bank to watch for fraudulent transfers and lock down accounts if the scammer had access. Monitor closely for unauthorized transactions.
Place Fraud Alert
Consider placing a fraud alert on your name with the credit bureaus so no accounts can be opened without your approval.
Report the Scam
File a complaint with the FTC about the Microsoft support scam call so they can help shut them down. Provide any details about the pop-up, phone number, and conversation.
Although falling victim is disheartening, take swift action to regain control. Disconnecting devices, removing malware, and securing accounts can help minimize damages from identity theft or financial fraud.
How to Remove Unwanted Apps and Malware
If you have accidentally downloaded unwanted programs or malware from a pop-up scam, you can find below a full malware removal guide.
Please perform all the steps in the correct order. If you have any questions or doubts at any point, stop and ask for our assistance.